Zscaler – Bypass Disable Service
| Title | Zscaler – Bypass Disable Service |
| Discovery date | 08/11/2021 |
| Release date | 04/11/2022 |
| Credits | Almaviva Cyber Defence Threat Center |
| Affected products | Zscaler Client Connector |
| Class | Bypass business logic |
Disclosure timeline
| 08/11/2021 | First report of vulnerability to zscaler |
| 11/10/2022 | Second report of vulnerability to zscaler |
| 04/11/2022 | Request for CVE ID (Not Assigned) |
| 10/11/2022 | JCV-2022.11.10.02 released |
Vulnerability details
This vulnerability allows the user to rename the system folders of the Zscaler Client Connector, blocking the services’ restart, configuring the agent in Turn Off and to navigate the web while avoiding the requests’ redirect through the protected tunnel.
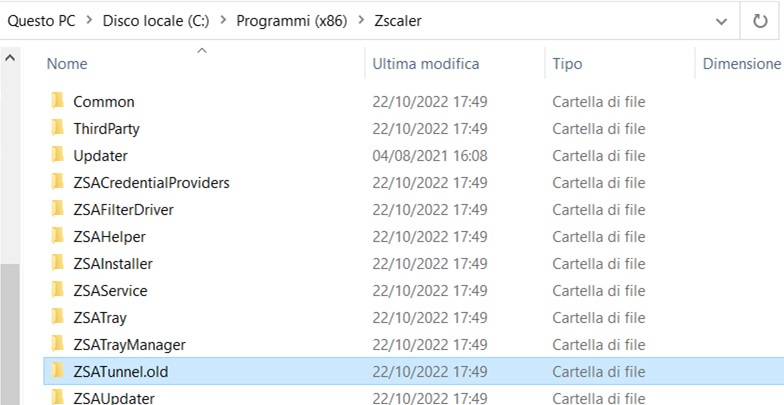
Inside the product’s folder, that by default is C:\Program Files (x86)\Zscaler, you can find the ZSAService folder. By modifying said folder, ZScaler will not be able to function, de facto disabling its protection.
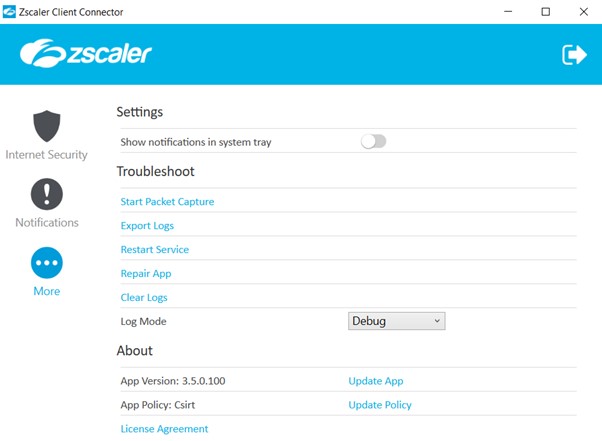
By accessing the ZScaler Client Connector interface and going on the “More” menu, you can force a restart of the services via “Restart Service”. The agent will try to restart it, but it will inevitably fail:
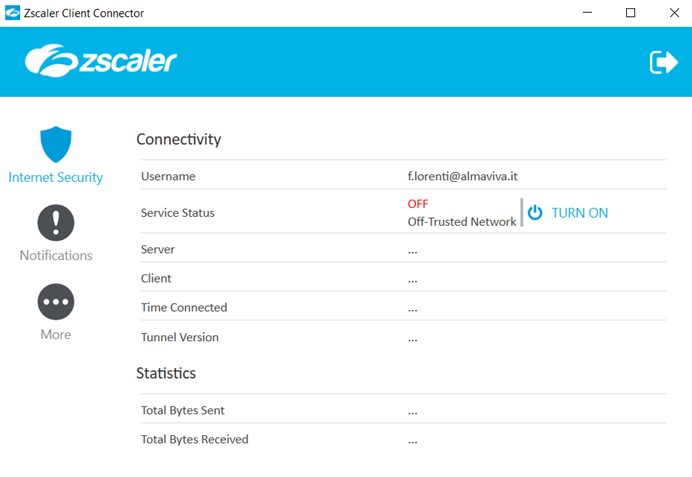
Not capable of repristinating the necessary services, the ZScaler Agent will be set to OFF, not allowing the ZScaler Internet Access manager to detect anomalies.