PwnDoc – Up to (including) 0.5.3
| Title | PwnDoc – Up to (including) 0.5.3 |
| Discovery date | 24/10/2022 |
| Release date | 29/10/2022 |
| Credits | Lorenzo Anastasi |
| Affected products | PwnDoc, version: up to (including) 0.5.3 |
| Class | Username Enumeration via response timings |
Disclosure timeline
| 24/10/2022 | Tried to reach out project’s contributors (no contact available publicly) |
| 24/10/2022 | Opened issue on GitHub |
| 26/10/2022 | Request for CVE ID |
| 29/10/2022 | CVE-2022-44022 released |
Vulnerability details
Username Enumeration via response timings in PwnDoc (up to and including 0.5.3) allows unauthenticated attacker to enumerate users, registered on the web platform, observing the web server response timings.
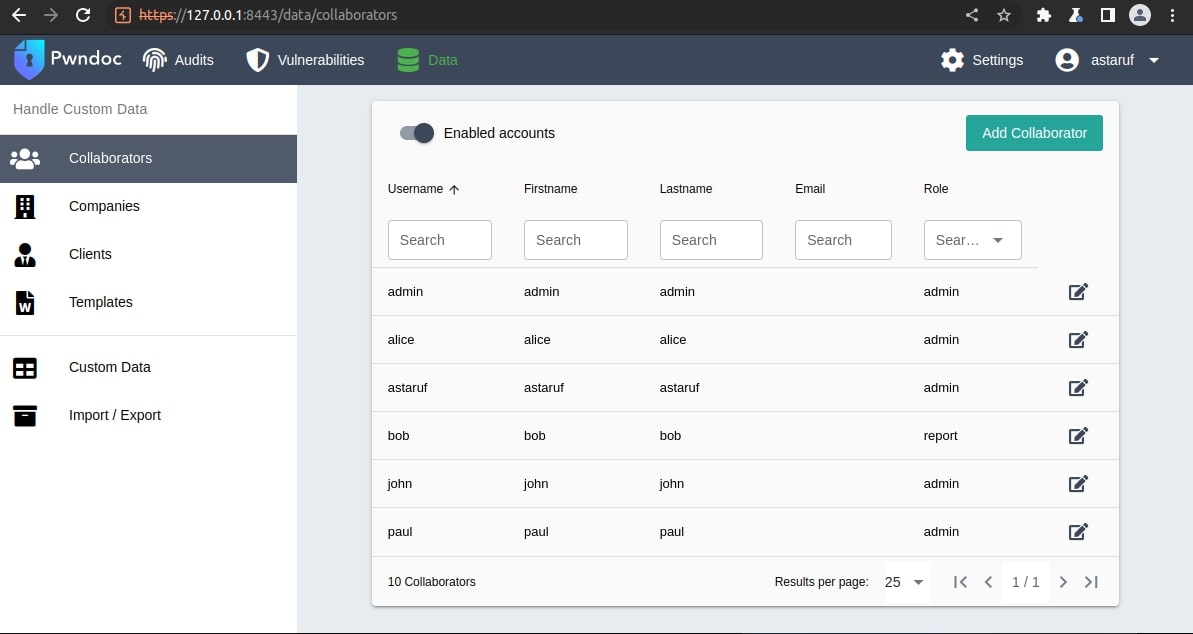
Let’s suppose these users were registered in a PwnDoc instance:
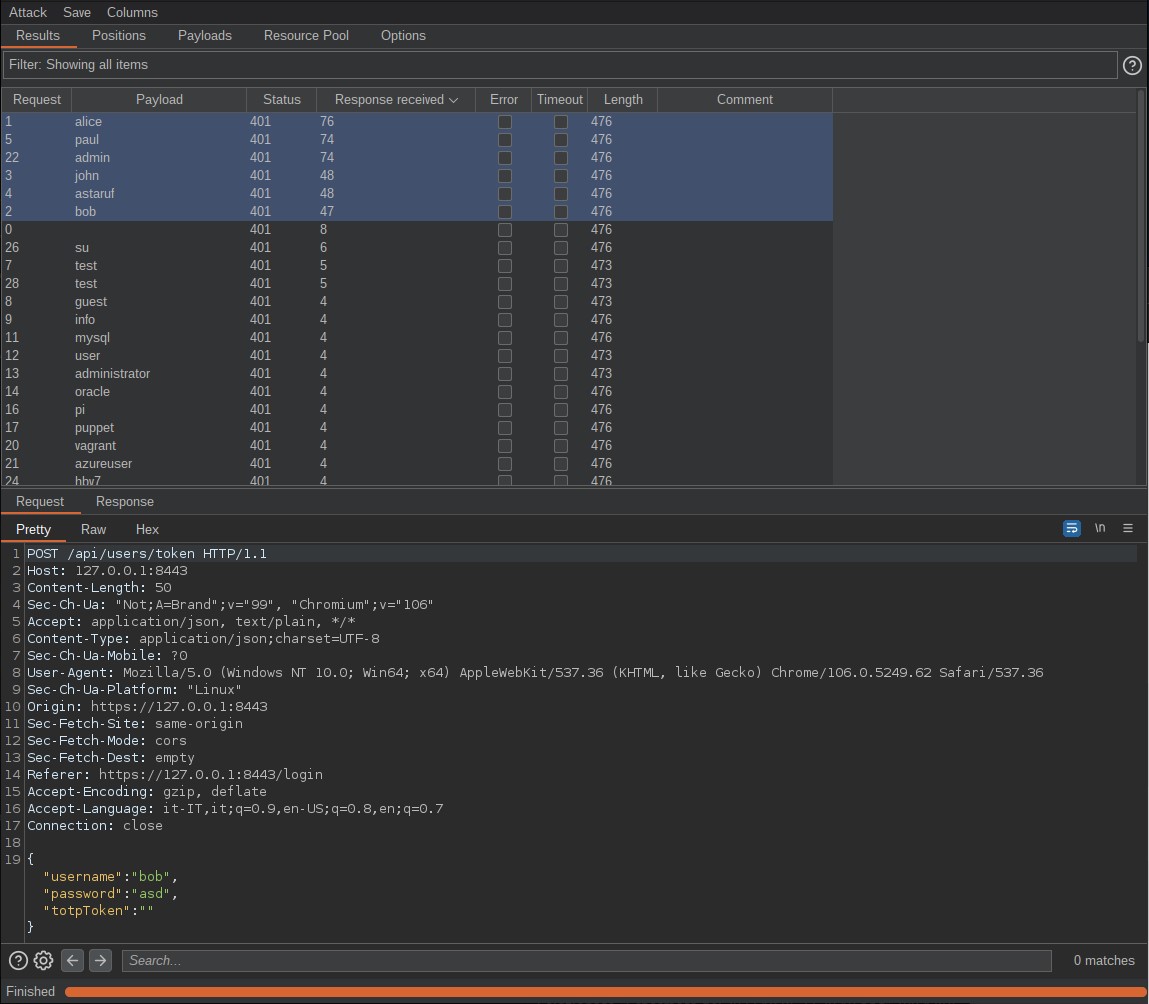
By performing a brute force dictionary attack, a defined list of users can be provided via login POST request to detect the server’s response time.
All the valid users can be discovered by a potential attacker checking if the response time to the login request is long. For not-existing users we can see a shorter response time.
The attack success depends higly on the stability of the server and the Internet connection between hosts. In any case, in order to apply a remediation, it is advisable to add a timing delay to balance the response timing for each login request.